What is a Browser Hijacker?
Browser hijackers are a form of malware that attacks and hijacks web browsers. They take the form of malicious browser add-ons or plugins. The threat actors attack browsers so that they have as large a target to aim for as possible. By hijacking browsers and not operating systems, the threat actors don’t need to write a version of their malware for the Windows, Linux, and Mac platforms.
Regardless of the type of computer you use, you’ll still use a browser. Attacking browsers lets the threat actors produce what is effectively platform-agnostic malware.
Techopedia Explains
You can catch a browser hijacker from a malicious attachment on an email, downloading infected files, visiting a website that is designed to infect visitors, or visiting a legitimate website that has been compromised by the threat actors so that it dispenses their browser hijacker.
Browser hijackers override your browser’s settings to change its behavior. You may see a new home page, a new toolbar, or a change in your default search engine. These changes will put false entries in web search results and redirect (via a redirect virus) you to specific websites. The hijackers sometimes make modifications to your computer’s registry so that the hijackers are difficult to remove.
The owners of websites pay the malware authors a small amount per visitor, in a similar way to adware. The hijacker authors try to do what they can to herd internet traffic to the websites that will pay them. The websites may contain material that is fraudulent, indecent, or that can infect you with malware.
How Hijackers Affect Your Computer
Once the browser hijacker has installed itself in your browser, it will use some or all of these methods to protect itself and control your browser.
Modifying Your Browser’s Behavior
A browser hijacker might change the appearance of your browser, the behavior of your browser, or both. Visual signs might include:
- A new home page
- A new default search engine
- A new toolbar
- A strange website when you create a new tab
- New favorites or bookmarks and old bookmarks may be removed
Behavioral changes can include:
- A lot of popup adverts
- Bogus entries in your search results
- Legitimate websites can’t be reached, especially websites owned by antivirus and antimalware companies
- A drop in browser performance
These changes are intended to drive you to particular websites and to prevent you from reaching websites that may offer assistance or advice in removing the hijackers.
Data Collection
Browser hijackers track your browsing behavior and collect keystrokes. The data is sent to the threat actors. The type of information a hijacker can collect about you includes:
- Search terms you have used
- Websites that you have visited
- Which files you have uploaded, and to which sites
- Which files you have downloaded, and from where
- Sensitive information such as login credentials and credit card details
The collected information is either used by the threat actors to perpetrate identity theft and fraud, or it can be sold to other criminals.
Digging in Deep
Browser hijackers don’t make it easy for you to remove them. They don’t have an uninstall option, for example. They can use registry hacks and other persistence tricks to make sure they are very difficult to remove.
Some of them will have installed small helper programs or browser helper objects that will reinstall the hijacker if it is removed.
Performance Loss
Many browser hijackers are quite poorly engineered by the threat actors who write them. They don’t care if they introduce a strain on your browser and reduce its performance. Because they don’t care, they don’t try to engineer ways around the issue.
They leave their code as it is, and you have to put up with the degraded performance.
Always Keep Your Browser Updated
Make sure you update your browser frequently to benefit from the security improvements each new release has. Google Chrome and Firefox are updated around every 40 to 50 days. Microsoft Edge is updated with Windows on an approximate six-week cycle. So all of the big three browsers have a similar update cycle.
How To Remove Browser Hijackers
So you got hit and want to know how to get rid of a browser hijacker. Browser hijacker removal can be as simple as resetting your browser to a fresh state, but try contacting a professional or using an anti-malware tool first. Here’s what you need to know.
- If you have an IT department or support team, you can call on, do so, and let them handle it.
- If you have an anti-malware tool installed as part of your endpoint protection, try running a scan with that tool. That might remove the hijacker for you.
- If the hijacker is still present after the scan, a web search –performed on a different computer – might return a specific removal tool for the version of the browser hijacker that you have been infected with. If you find one, only trust it if it is produced and available for download from a reputable security site, such as a big-name antivirus company. Posing as a benign malware-removal tool is a well-known ploy used to spread malware.
- If you have to, you can try manually removing the hijacker by hand. You can restore a modern browser to its “fresh install” state.
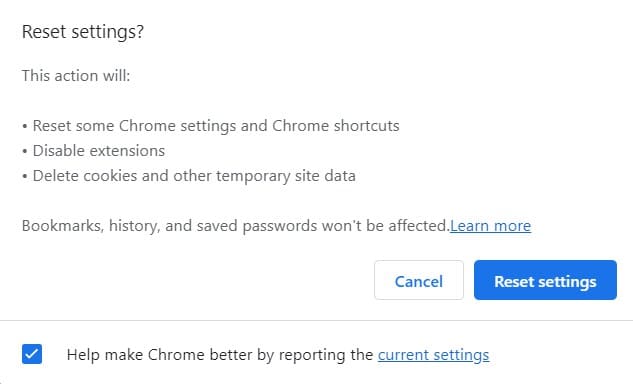
Resetting Chrome
To remove a browser hijacker from Chrome, copy and paste this line into the address bar:
When you press “Enter,” you will see the “Reset Settings” dialog box.
Click the blue “Reset Settings” button to restore Chrome to its original settings.
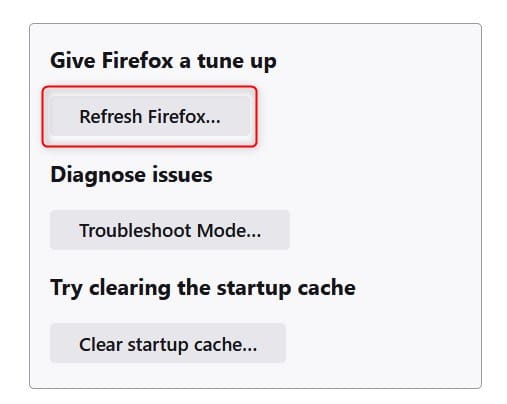
Resetting Firefox
To reset Mozilla Firefox, copy and paste the following line into the address bar:
When you press “Enter,” you will see the “Troubleshooting Information” page. In the top-right corner, you’ll see the “Give Firefox a tune-up” pane.
Click the gray “Refresh Firefox” to reset the browser settings.
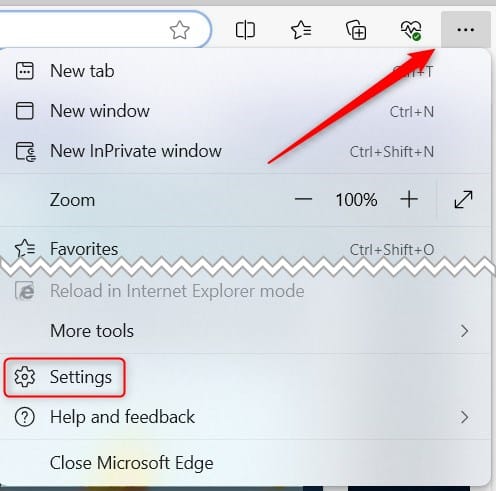
Resetting Microsoft Edge
To reset Microsoft Edge, click the three-dot menu icon “…” and select “Settings” from the drop-down menu.
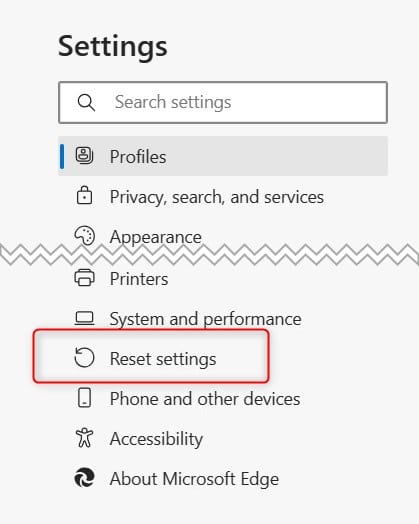
Select the “Reset Settings” option from the left-hand pane.
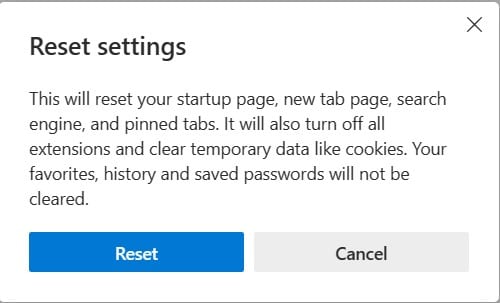
The “Reset Settings” dialog will appear. Click the blue “Reset” button.
Your browser settings will be restored to their default settings.
Resetting Mobile Devices
If the infected device is a tablet, smartphone, or Chromebook that stores all of its data in the cloud, it is probably easier to factory reset your device and then download your data from the cloud.
Prevention is Better Than the Cure
- Obey any warnings that your browser might show about websites that you’re trying to visit. If they say the site is suspicious or insecure, you probably don’t want to proceed to that website.
- Don’t download files or software from anywhere other than official sites.
- Check the small print in the terms and conditions when you install software, and make sure you’re not agreeing to allow it to install “other software from time to time” or equally vaguely worded clauses.
- When you’re installing software, read each page of the installation routine carefully. Don’t just click “Next, Next, Next” to go through the process as fast as possible. Make sure you don’t inadvertently give permission for extra toolbars and other software.
- Consider using a JavaScript blocker. The Chrome ScriptBlock extension and the Firefox NoScript Security Suite both block JavaScript but let you enable JavaScript temporarily, at your discretion, with a single click.
- Do a bit of research before installing a browser add-on or extension. How many users does it have, when was it last updated, and what do the reviews say? If you do a web search on their name, do you see any worrying or negative comments?